Recon Rundown #1 : Attack Surface Basics

Introduction
The first step of hacking computers is finding computers. While conceptually this seems simple enough, the reality is that it's far from easy or straightforward. From working around whois protection to bypassing Cloudflare, things get very crazy very quickly.
This year, I've challenged myself to create and release one thing every week, most of which will probably be focused around web reconnaissance in some way. I figured the best place to start is here with the basics so that those who want to follow along will head into the later, more advanced content having already learned the foundational pieces of how the internet works.
With that out of the way, let's get into it!
Domains
The domain (e.g. apple.com) can be considered the most basic unit of information in the world of web reconnaissance.
Using the whois command on Linux or a site like whoxy.com, we can retrieve information about the owner of the domain (although domain owners can also choose to keep this information private.)
➜ whois apple.com
Domain Name: apple.com
Updated Date: 2021-02-16T01:26:20Z
Creation Date: 1987-02-19T00:00:00Z
Registry Expiry Date: 2022-02-20T05:00:00Z
Registrant Name: Domain Administrator
Registrant Organization: Apple Inc.
Registrant Street: One Apple Park Way
Registrant City: Cupertino
Registrant State/Province: CA
Registrant Phone: +1.4089961010
Registrant Email: domains@apple.com
Name Server: a.ns.apple.com
Name Server: b.ns.apple.com
Name Server: c.ns.apple.com
Name Server: d.ns.apple.com
Whoxy also has a neat option to do "reverse whois" searches, where we can take one of these pieces of information, and see what other domains have been registered using it. Doing this for the email address domains@apple.com turns up a LOT of results, as seen below.
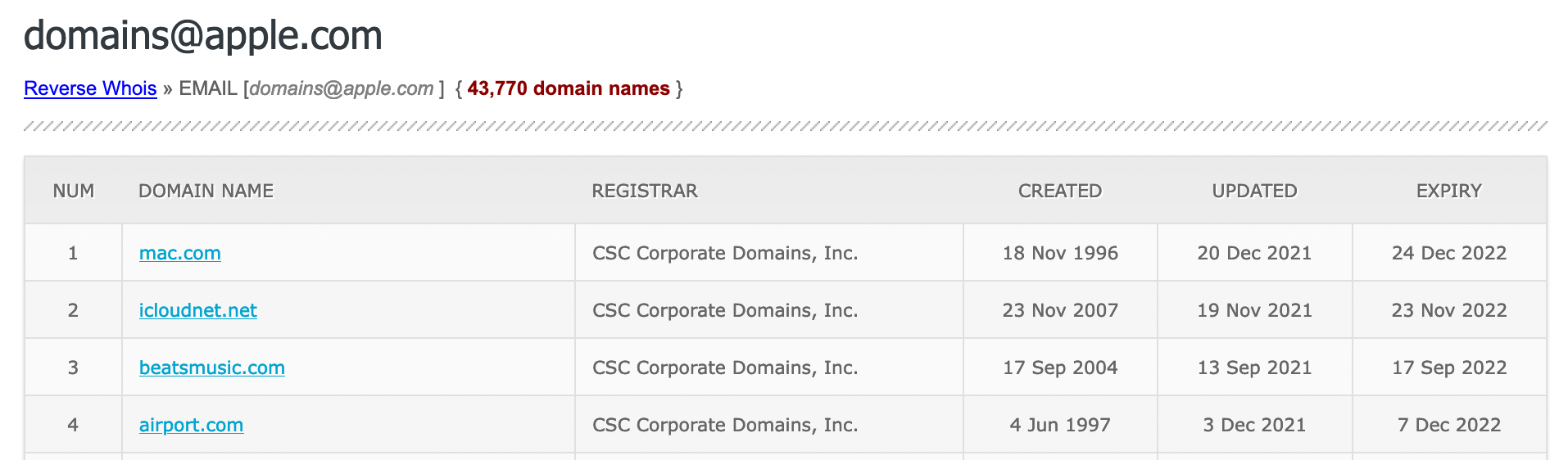
Name Servers
As we saw in the whois output above, there's a lot of pieces of information here that we can use to pivot off of. But what do we do if a domain has private registration?
➜ whois hackerone.com
Domain Name: HACKERONE.COM
Updated Date: 2021-08-29T11:00:02Z
Creation Date: 2007-11-26T19:45:36Z
Expiration Date: 2022-11-26T19:45:36Z
Registrant Name: DATA REDACTED
Registrant Organization: DATA REDACTED
Registrant Street: DATA REDACTED
Registrant City: DATA REDACTED
Registrant State/Province: CA
Registrant Postal Code: DATA REDACTED
Registrant Country: US
Registrant Phone: DATA REDACTED
Registrant Phone Ext: DATA REDACTED
Registrant Fax: DATA REDACTED
Registrant Fax Ext: DATA REDACTED
Name Server: a.ns.hackerone.com
Name Server: b.ns.hackerone.com
Well we're in luck because HackerOne is running their own name servers! Name servers are responsible for turning subdomains (like docs.hackerone.com) into actual IP addresses our computer can request data from (like 185.199.109.153.)
Using a site like DNSlytics we can perform a reverse name server lookup to see what other domains are using a.ns.hackerone.com as their name servers.
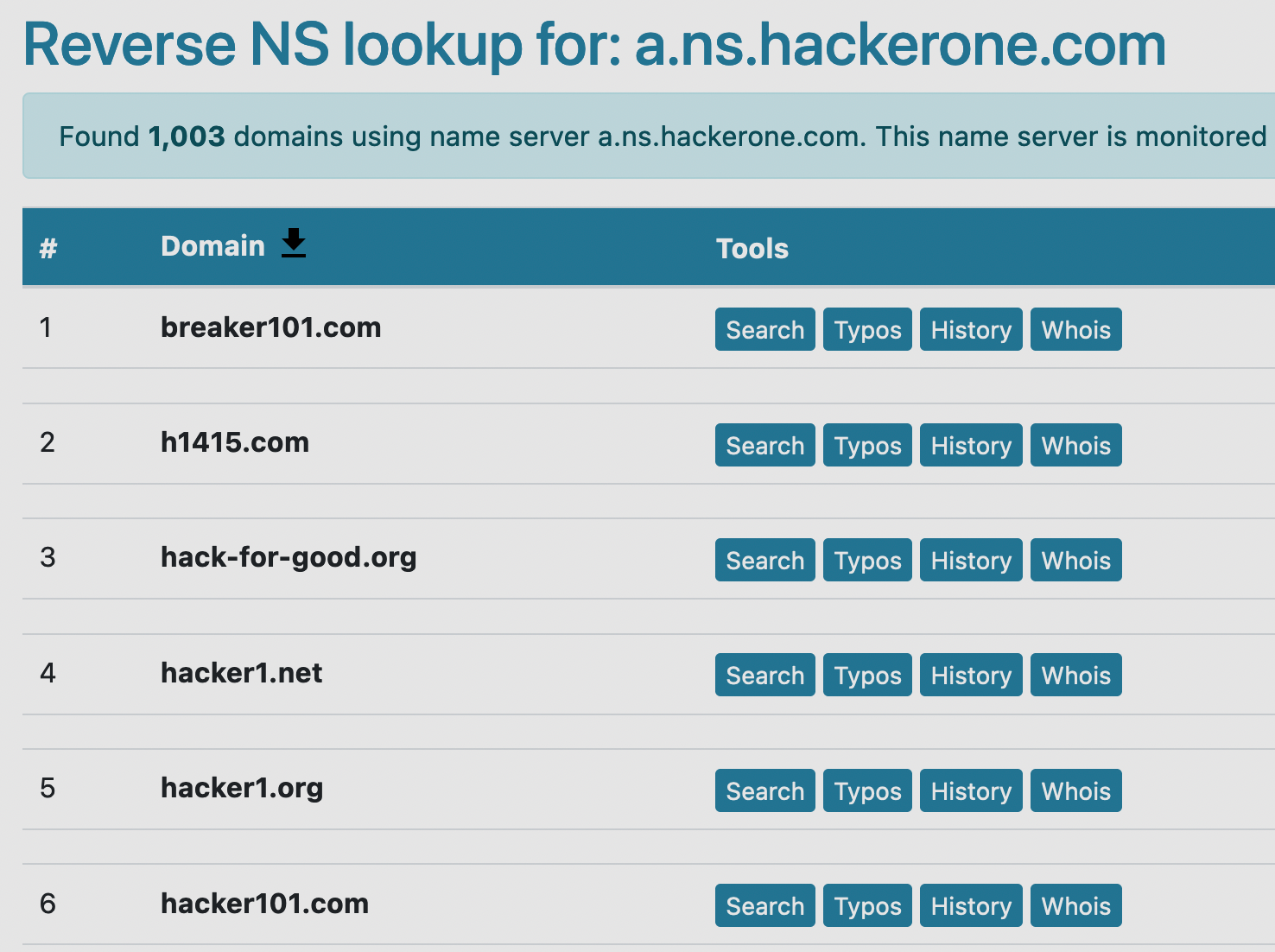
With this simple trick, we were able to find other domains with the same owner (HackerOne) that also have private whois information. While this won't always be the case, it's still very helpful to create a more complete picture of a company's attack surface.
If you're interested in learning more about how name servers work and the rest of the wild world of DNS, Cloudflare has an easy to understand, but very thorough explanation you can read through on their site.
Subdomains
If domains are the most basic unit of recon, subdomains are the most useful. Each subdomain is usually a different application, as we can see by browsing to ads.google.com and store.google.com. We can also use the dig tool in Linux to see that both of these also point to different IP addresses.
➜ dig +short ads.google.com
142.250.191.78
➜ dig +short store.google.com
142.251.46.206
On Github you can find approximately fifty million tools people have made to find subdomains, and there's about fifty million more APIs and online tools for getting the job done. Ultimately most of them work by integrating the same few sources or techniques:
- Rapid7's fDNS Dataset
- A TLS certificate search engine like crt.sh
- Brute force, using a VERY large list of potential subdomains.
IP Address Blocks and ASNs
One of the final pieces required to get a comprehensive picture of a company's attack surface is figuring out what IP addresses they own. Many of these assets don't have subdomains pointed to them and would be otherwise impossible to find and track externally if not for public ownership records. One of the most popular sites to look up this information is bgp.he.net.
There are three main structures that are important to know here:
- The single IP address,which can be thought of as a street address for a computer
- The netblock (a.k.a network prefix, CIDR range, etc.), which is a group of neighboring IP addresses that can be thought of almost like a city block.
(Note: the91.224.159.0/24here means the 256 IP addresses from91.224.159.0-255) - The autonomous system number (ASN), which consists of one or more netblocks and can be though of as a town/city.
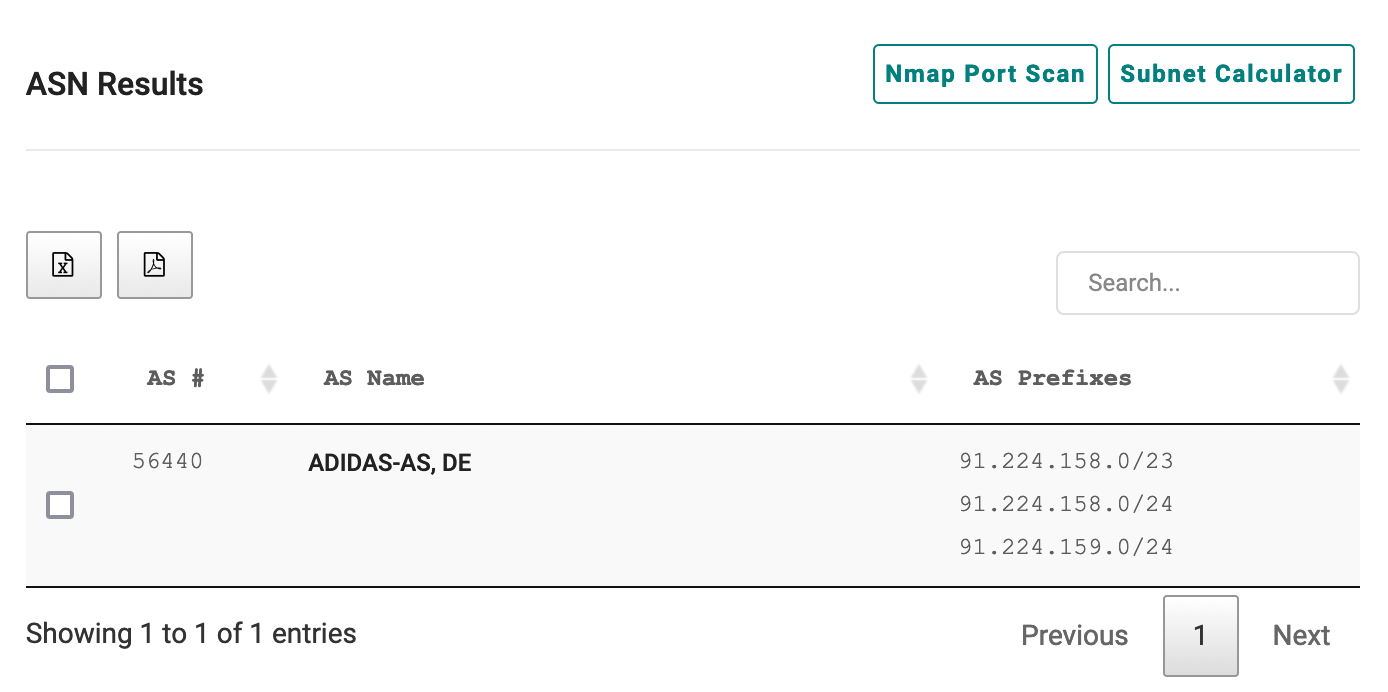
In the screenshot above, we can see an example of this structure using Adidas as an example. Adidas owns additional ASNs as well, but we're focusing on just this one for the sake of this example.
Conclusion
This has been just a very basic overview of the way different bits of information relate to each other, and how we can use those pieces to better understand the attack surface of a company.
In upcoming blogs we'll learn about how we can use some of these relationships in new and interesting ways, like using reverse DNS lookups to see what domains point back to a specific netblock!
Tools used in this Article
- Reverse Whois Lookups
- ASN Lookups
- Reverse NS Lookups
- Sources for Subdomain Data
- DNS Brute Forcing Wordlists
- Subdomain Enumeration Tools
No spam, no sharing to third party. Only you and me.

